Assumptions of Deployment Architecture
- The Power BI model and reports are located in the same workspace.
- Reports utilize a shared semantic model.
- All reports are published via a Power BI app for end users.
Solution Summary:
Enforce Robust Security Controls – Implement both Row-Level Security (RLS) and report-level access restrictions.
Streamline Model Management – Maintain a single shared semantic model with built-in security to reduce maintenance overhead while ensuring compliance.
Ensure Strict Access Control – Guarantee that users can only access the data and reports they are authorized to view.
Detailed Requirements:
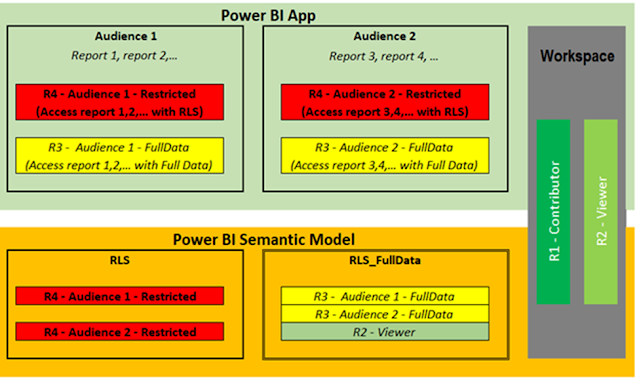
There are four roles with different access requirements. The diagram below illustrates the access structure.
Challenges & Analysis:
While roles 1, 2, and 4 have straightforward solutions, role 3 presents a unique challenge. Below are three potential approaches and their drawbacks:
Option 1: Assign Role 3 as "Contributors" in the Workspace
Issue: Contributors have access to all reports via the Power BI app, and restricting access at the report level is not possible.
Conclusion: This approach does not meet the requirement for selective report access.
Option 2: Use a Security Dimension to Control Access
Challenges:
The security dimension could become excessively large, as it would need to store permissions for all users.
Dynamic updates would be required to ensure new users and changing data permissions are accurately reflected.
The security dimension might not cover all records due to incomplete mappings, potentially filtering out critical data.
Conclusion: This approach is impractical due to scalability and data completeness issues.
Option 3: Duplicate the Semantic Model
Process:
Create two versions of the semantic model: one with RLS and one without RLS.
Maintain separate reports pointing to each model, respectively.
Configure Power BI app audiences accordingly.
Challenges:
Requires maintaining duplicate models and reports.
Increases complexity in Power BI app configuration.
Conclusion: This approach introduces high maintenance overhead and redundancy.
Optimized Solution:
Rather than adopting the flawed approaches above, we propose an innovative RLS setup that does not impose restrictions. The key steps include:
Define an RLS Role with Full Access:
The security filter is set to
TRUE(), ensuring that assigned users can access all data without restriction.
Use a Disconnected Security Dimension:
Applying
TRUE()alone is insufficient because relationships between the security dimension and the main model may still filter data unexpectedly.By using a disconnected security dimension, we prevent unintended filtering effects.
This approach achieves:
No need for a massive security dimension.
No need for duplicate models.
No need for duplicate reports.
Simplified Power BI app configuration.
With this methodology, along with the existing roles 1, 2, and 4, the final solution structure is illustrated below
Implementation Steps:
Create an RLS Role (Refer to the diagram below).
- Define security groups based on role-based access needs
- Extend security group assignments as necessary (Refer to the attached diagram).
This solution ensures scalable, maintainable, and efficient security management within Power BI, aligning with the business requirements for secure and streamlined report access.
Note 1: “Apply security filter in both directions” ensures row-level security filters flow both ways across the relationship, which can be powerful but might complicate your security model.Turn on both-direction filters only when you need dimension tables to be filtered based on row-level security rules that originate in the fact table or in other scenarios that require the dimension table itself to be restricted by fact data.




No comments:
Post a Comment